Technology and Society
Technology affects the way individuals
communicate, learn, and think. Technology has both
positive and negative affects on society including
the possible improvement or declination of society.
Society is defined as, "the sum of social
relationships among human beings" and
technology is defined as, "the body of knowledge
available to a civilization that is of use in fashioning
implements, practicing manual arts and skills, and
extracting or collecting materials." Technology
shapes our society and has both positive and
negative affects.
Societal issues and cultural changes induced by technology
Social issues:-
1. Identity Theft
2. Cyber Bullying
3. Gaming Addiction
4. Privacy
5. Health & Fitness
6. Education
7. Terrorism & Crime
8. Communication Breakdown
9. Defamation of Character.
Societal issues and cultural changes induced by technology
Cultural changes–
Technology has completely changed our culture. From our
values, To our means of communication. Now, Many people
have trouble having a face to face conversation, Skype does
not count. When people spend time with friends, Its on their
phones, Tablets, Or computers. Also, Now people judge
others by how techy their car is, Or if they have the newest
iPhone or Tablet Most people want to put their headphones in
and listen to music rather than listening to another person.
Videogames isolate all things from the world. Most people
prefer technology today, Just because that is all they know.
Today it’s all about touch screen cell phones. Technology just
isolates people from reality. People now a days don’t know
how to communicate in real world situations like personal
relationships, Problem solving and exhibiting adult behaviors.
Let’s take the daily personal view here:
- Every time a notification pops up on our phone or computer, that’s technology influencing culture.
- Every time we at a table with our friends and interacting with them and interacting with our phone, that’s technology influencing culture.
- Every time we can order something from an online vendor rather than going to a local store, that’s technology influencing culture.
- Every time we log on to have some social time with friends rather than going over to their houses, that’s technology influencing culture.
- Every time a teammate or our entire team is so buried under email that they can’t think straight, that’s technology influencing culture.
- Every time we go to a new place based on its Yelp profile and reviews, that’s technology influencing culture.
- Every time one of us sits down to consume our nightly on-demand entertainment, that’s technology influencing culture.
E-waste Management
Whenever an electronic device covers up its working life, or
becomes non-usable due to technological advancements or
becomes non-functional, it is not used anymore and comes under
the category of e-waste or electronic waste. As the technology is
changing day by day, more and more electronic devices are
becoming non-functional and turning into e-waste. Managing such
non-functional electronic devices is termed as e-waste
management.
E-waste management can be defined as the practical and holistic
approach and the founding pillar of cutting down waste from our
mother earth. It is reusing and recycling of e-waste which is no
longer in use and can be salved for some of its components. We are
on the verge of a technological breakthrough with the introduction
of AI and we need to dispose off toxic e-waste from our home before
we pile up more and more e-waste. We are is dire need of
introducing a customer awareness campaign because of lack of
interest and knowledge regarding e-waste.
Proper disposal of used electronic gadgets
E-waste is a growing problem for us in India. As an 132cr
strong economy, we produce e- waste in large quantities.
It is very important to dispose off waste in a pragmatic
manner.
Ways to dispose off e-waste:
1. Give Back to Your Electronic Companies and Drop Off
Points
2. Visit Civic Institutions
3. Donating Your Outdated Technology
4. Sell Off Your Outdated Technology
5. Give Your Electronic Waste to a Certified E-Waste
Recycler
Identity theft
Identity theft occurs when someone uses our identity or
personal information—such as our name, our license, or
our Unique ID number—without our permission to
commit a crime or fraud.
Common Ways ,how our Identity Can Be Stolen:
- Data Breaches
- Internet Hacking
- Malware Activity
- Credit Card Theft
- Mail Theft
- Phishing and Spam Attacks
- WiFi Hacking
- Mobile Phone Theft
- ATM Skimmers
Common Ways our Identity is Used:
- Thieves open fraudulent credit card accounts in our name.
- Thieves use our credit cards or account numbers to make purchases.
- Thieves sell our personal information on the dark web—Unique ID no, credit card, and account information—to commit credit fraud, medical fraud and more. Thieves file fraudulent taxes and/or steal our tax refunds.
- Thieves know your account passwords, bank PIN numbers or other passwords to access your computer
How to protect identity online:
- Protect our computer and smartphone with strong, upto-date security software Learn to spot spam and scams.
- Use strong passwords.
- Monitor our credit scores
- Freeze our credit.
- Only use reputable websites when making purchases
Steps immediate after identity theft :
- Contact our lender, notify them of the fraud. If it’s a credit card account, freeze your card immediately.
- Register an FIR with the police.
- Follow up with the lender to ensure that the fraudulent transaction (if it appears) the FIR is removed.
Unique IDs and biometrics
Biometrics is the science of analyzing physical or behavioral
characteristics specific to each individual in order to be able to
authenticate their identity.
- Physiological measurements -They can be either morphological or biological. These mainly consist of fingerprints, the shape of the hand, of the finger, vein pattern, the eye (iris and retina), and the shape of the face, for morphological analyses.
- Behavioral measurements -The most common are voice recognition, signature dynamics (speed of movement of pen, accelerations, pressure exerted, inclination), keystroke dynamics, the way objects are used, gait, the sound of steps, gestures, etc. A unique identifier (UID) is a numeric or alphanumeric string that is associated with a single entity within a given system. UIDs make it possible to address that entity, so that it can be accessed and interacted with.
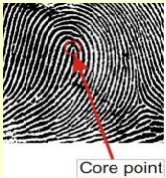
Unique ID Generation: An image processing tool like MATLAB is used for the conversion of
fingerprint to unique ID in the form of a QR code. The most important step
is to identify a unique point in the fingerprint which will serve as a
reference point. All the other minutia features will be calculated with this
point as the origin. And hence the fingerprint of the same individual taken
in different orientations will all produce the same ID. Core point of the
fingerprint is one such unique point.
After finding the core point, the minutia points are extracted by taking the
core point as reference. there will be a large number of minutiae. But only
a few minutiae which are absolutely unique for that particular fingerprint is
needed to generate the unique ID. For this only the minutiae which are
inside a Region Of Interest (ROI) centered around the core point are taken.
The reliability of biometrics
- Biometric authentication relies on statistical algorithms. It therefore cannot be 100 %-reliable when used alone. "false rejections" or "false acceptances“.
Multi-modal biometrics:
- For a number of years now, the use of several biometrics in combination, for example the face and the iris or the iris and fingerprints, has made it possible to reduce error rates considerably.
How accurate is biometrics?
- The technical challenges of automated recognition of individuals based on their biological and behavioral characteristics are inherent in to the transformation of analog (facial image, fingerprint, voice pattern...) to digital information (patterns, minutiae) that can then be processed and compared/matched with effective algorithms.
Gender and disability issues while teaching/using computers
Gender Issues
- Preconceived notions – Notions like “boys are better at technical and girls are good at humanities.
- Lack of interest
- Lack of motivation
- Lack of role models
- Lack of encouragement in class
- Not girl friendly work culture
Issues list above are not intentionally created , hence need a different type
of handling
- There should be more initiative program for girls to take computer subject.
- Film and tv censor board should ensure fair representation of female role models in tv or cinema
- In practical room they should be more helped and assisted
Disability Issues
- Unavailability of teaching materials/aids
- Lack of special needs teachers
- Lack of supporting curriculum
Possible Solution
- Enough teaching aids must be prepared for specially abled students
- Must employ special needs teachers
- Curriculum should be designed with students with specially abled students in mind.

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.