This blog contains short notes , practice exercise for XI and XII CBSE IP subject.
Tuesday, November 19, 2019
Monday, October 21, 2019
Society, Law , Ethics- Part-III
Role of new media in society
New Media – Means mass communication using IT tools
and techniques/digital technologies such as Internet.
Reason of attraction/Advantages of new media-
- On demand availability
- Any time availability
- Any place availability
- Convertible as per device
- Multiple forms of express(audio/video/animation/text etc.)
- Fast spread/easily sharable
- Interactive(readers can submit their feedback/reviews)
Forms of new media
- Internet
- Websites
- Computer multimedia
- Social networking
- Video games
- Blogs
Disadvantages of new media
- Not a reliable source to get news from
- Privacy issues
- Cyber bullying
An Online Campaign involves showing
ads/message/popup online for a specific product/service
or any specific cause in a specific time period. An online
campaign can be used to show ads/message/popup on
multiple websites, and in many formats, but they will all
advertise the same product/service or idea.
Online Campaign can deliver benefits such as:
- Growth in potential
- Reduced expenses
- Elegant communications
- Better control
- Improved customer service
- Competitive advantage
Step of Online campaign
Step
- Identify Customer Step
- Choose Your Targets Step
- Budget Step
- Creating campaign Content Step
- Tracking and Monitoring campaign/ads
Disadvantages/limitations of online campaign
- Customers Ignore Ads
- Viewing Problems
- Expensive Ad Prices
- Consumers Get Distracted
- Too Many Options
- Face-to-Face Contact is Limited
Crowdsourcing
Crowdsourcing is a term used to describe the process of
getting work or funding from a large group of people in an
online environment. While the idea behind crowdsourcing
isn’t new, but it’s active use is around 2006. The phrase
was initially coined by Jeff Howe, where he described a
world in which people outside of a company contribute
work toward that project’s success. Video games beta
version are perfect example of crowdsourcing. Granting
players early access to the game to find out bugs before
the finished product is released for sale and distribution.
Crowdsourcing is a powerful business marketing tool to
leverage the creativity and resources of its own audience
in promoting and growing the company for free.
Types of crowdsourcing
- Crowd contest - In this case, an organization may use a crowd contest to create something, such as a graphic design.
- Macrotasking - seek out many respondents, assigning each one some task or a smaller part within a larger project.
- Crowdfunding- in which individuals or nonprofits ask for money to cover the costs of an identified endeavor.
- Crowd votes - to determine the best. Entities may opt to use crowd voting to engage stakeholders to determine a course of action.
The downsides of crowdsourcing consumers involved as crownsource aren’t employees, which means organizations can’t contain or control them.
Smart Mob
smart mob
a large group of people mobilized by social media to meet in a public
place typically for the purpose of social or political protest.
The Battle of Seattle was one of the first examples of Smart Mobs. On
November 30 1999 protestors lined the streets of Seattle to protest
the WTO. The protestors were able to communicate with one another
by using technological devises such as websites, cell phones
laptops, radios, and other similar technologies.
The impacts of smart mob technology already appear to be both
beneficial and destructive, used by some of its earliest adopters to
support democracy and by others to coordinate terrorist attacks. The
technologies that are beginning to make smart mobs possible are
mobile communication devices and pervasive computing.
echo chamber
echo chamber - comfy little groups of like minded members in
any webapp / social media over internet is known as echo
chamber.
In today’s hyper connected world we’re all just a click away from
each other. This should be bringing us closer together. But,
increasingly, we’re finding ourselves pulled further apart as our
own natures push us into comfy little groups of like minded
members, or ‘echo chambers’.
Facebook, Twitter, Google and other internet services design
their algorithms to filter out what they think you don’t want to
see. They also provide the tools to let you exclude anyone who
irritates you.The result seals you up in online bubbles of
personally tailored content that make you feel safe and confident
and, importantly for these services, keep you engaged on their
sites for longer.
Net neutrality
Net neutrality is the principle that individuals should be free to access all
content and applications equally, regardless of the source, without
Internet Service Providers discriminating against specific online services
or websites. In other words, it is the principle that the company that
connects you to the internet does not get to control what you do on the
internet.
Columbia University law professor Tim Wu coined the term "network
neutrality" in a 2003 paper about online discrimination. At the time, some
broadband providers, including Comcast, banned home internet users
from accessing virtual private network
The Bush-era FCC took a first pass at anti-discrimination rules for the
internet in a policy statement in 2005. It prohibited internet service
providers from blocking legal content or preventing customers from
connecting the devices of their choosing to their internet connections.
Following are the indirect rules of net neutrality:-
- NO rules preventing blocking of website, services, or content online
- NO rules preventing throttling or slowing down of website or services online
- NO rules preventing paid prioritization where broadband providers give preferential treatment to some websites and services over others
Internet addiction
Internet addiction refers to the compulsive need to spend a lot of
time on the Internet, to the point where relationships, work and
health suffer.
Emotional symptoms of Internet Addiction Disorder -
Depression, Dishonesty, Feelings of guilt, Anxiety,Feelings of
Euphoria when using the Computer, Inability to Prioritize or Keep
Schedules, Isolation, No Sense of Time, Defensiveness,
Avoidance of Work, Agitation, Mood Swings, Fear, Loneliness,
Boredom with Routine Tasks, Procrastination .
Physical Symptoms of Internet Addiction Disorder –
Backache, Carpal Tunnel Syndrome, Headaches, Insomnia, Poor
Nutrition (failing to eat or eating in excessively to avoid being
away from the computer), Poor Personal Hygiene (e.g., not
bathing to stay online), Neck Pain, Dry Eyes and other Vision
Problems, Weight Gain or Loss.
Some of the more common psychological treatments of Internet
Addiction Disorder include:
- Individual, group, or family therapy
- Behavior modification
- Dialectical Behavioral Therapy (DBT)
- Cognitive Behavioral Therapy (CBT)
- Equine Therapy
- Art Therapy
- Recreation Therapy
- Reality Therapy
Case studies
Arab Spring
The term “Arab Spring” was popularized in early 2011 by the Western media, when
the successful uprising in Tunisia against former leader Zine El Abidine Ben Ali
emboldened similar anti-government protests in most Arab countries.
On December 17th, 2010, a Tunisian named Muhammad Bouazizi got into an
altercation with a Tunisian officer. It was reported that Bouazizi was selling fruit out
of a fruit cart within the city when the officer approached him and demanded that he
stop doing so, because he did not have a permit. Then, the two got into an argument,
and then, shortly after, the officer took his fruit cart. As it was reported, “It wasn’t the
first time it had happened, but it would be the last. Not satisfied with accepting the
10-dinar fine that Bouazizi tried to pay ($7, the equivalent of a good day’s earnings),
the policewoman allegedly slapped the scrawny young man, spat in his face and
insulted his dead father” (Abouzeid, 2011). And as Abouzeid (2011) writes for Time
Magazine, what happened afterwards was the defining moment in what would be one
of the largest protest movements the region has seen.
In July 2012 a report was published by the United States Institute of Peace based on
an extensive content analysis of bit.ly links from the uprisings in Tunisia, Egypt,
Libya, and Bahrain. Bit.ly links, or short URLs, are predominantly used in social
media such as Twitter. The authors came to some conclusions that countered the
initial assumption that social media was a causal mechanism in the uprisings.
WikiLeaks - a website intended to collect and share confidential
information on an international scale developed by Julian Assange, Born
in 1971 in Townsville, Australia, used his genius IQ to hack into the
databases of many high profile organizations. In 2006, Assange began
work on, and he earned the Time magazine "Person of the Year" title in
2010. Seeking to avoid extradition to Sweden over sexual assault
allegations, Assange was granted political asylum by Ecuador and holed
up at the country's embassy in London in 2012. In 2016, his work again
drew international attention when WikiLeaks published thousands of
emails from U.S. presidential candidate Hillary Clinton and the
Democratic National Committee. In April 2019, Assange's asylum was
rescinded and he was arrested in London.
Assange and WikiLeaks returned to the headlines during the summer of
2016 as the U.S. presidential race was narrowing to two main candidates,
Democrat Hillary Clinton and Republican Donald Trump. In early July,
WikiLeaks released more than 1,200 emails from Clinton's private server
during her tenure as secretary of state. Later in the month, WikiLeaks
released an additional round of emails from the Democratic National
Committee that indicated an effort to undermine Clinton's primary
opponent
Bitcoin is a cryptocurrency, or a digital currency, that uses rules
of cryptography for regulation and generation of units of
currency. Bitcoin falls under the scope of cryptocurrency and was
the first and most valuable among them. It is commonly called a
decentralised digital currency.
Bitcoin is a cryptocurrency, a form
of electronic cash. It is a decentralized digital currency without a
central bank or single administrator.
Bitcoins are completely virtual coins designed to be ‘selfcontained’ for their value, with no need for banks to move and
store the money.
Once you own bitcoins, they possess value and trade just as if
they were nuggets of gold in your pocket. You can use your
bitcoins to purchase goods and services online, or you can tuck
them away and hope that their value increases over the years.
Bitcoins are traded from one personal 'wallet' to another.A wallet
is a small personal database .
Sunday, October 20, 2019
Society, Law, Ethics: Part-II
Technology and Society
Technology affects the way individuals
communicate, learn, and think. Technology has both
positive and negative affects on society including
the possible improvement or declination of society.
Society is defined as, "the sum of social
relationships among human beings" and
technology is defined as, "the body of knowledge
available to a civilization that is of use in fashioning
implements, practicing manual arts and skills, and
extracting or collecting materials." Technology
shapes our society and has both positive and
negative affects.
Societal issues and cultural changes induced by technology
Social issues:-
1. Identity Theft
2. Cyber Bullying
3. Gaming Addiction
4. Privacy
5. Health & Fitness
6. Education
7. Terrorism & Crime
8. Communication Breakdown
9. Defamation of Character.
Societal issues and cultural changes induced by technology
Cultural changes–
Technology has completely changed our culture. From our
values, To our means of communication. Now, Many people
have trouble having a face to face conversation, Skype does
not count. When people spend time with friends, Its on their
phones, Tablets, Or computers. Also, Now people judge
others by how techy their car is, Or if they have the newest
iPhone or Tablet Most people want to put their headphones in
and listen to music rather than listening to another person.
Videogames isolate all things from the world. Most people
prefer technology today, Just because that is all they know.
Today it’s all about touch screen cell phones. Technology just
isolates people from reality. People now a days don’t know
how to communicate in real world situations like personal
relationships, Problem solving and exhibiting adult behaviors.
Let’s take the daily personal view here:
- Every time a notification pops up on our phone or computer, that’s technology influencing culture.
- Every time we at a table with our friends and interacting with them and interacting with our phone, that’s technology influencing culture.
- Every time we can order something from an online vendor rather than going to a local store, that’s technology influencing culture.
- Every time we log on to have some social time with friends rather than going over to their houses, that’s technology influencing culture.
- Every time a teammate or our entire team is so buried under email that they can’t think straight, that’s technology influencing culture.
- Every time we go to a new place based on its Yelp profile and reviews, that’s technology influencing culture.
- Every time one of us sits down to consume our nightly on-demand entertainment, that’s technology influencing culture.
E-waste Management
Whenever an electronic device covers up its working life, or
becomes non-usable due to technological advancements or
becomes non-functional, it is not used anymore and comes under
the category of e-waste or electronic waste. As the technology is
changing day by day, more and more electronic devices are
becoming non-functional and turning into e-waste. Managing such
non-functional electronic devices is termed as e-waste
management.
E-waste management can be defined as the practical and holistic
approach and the founding pillar of cutting down waste from our
mother earth. It is reusing and recycling of e-waste which is no
longer in use and can be salved for some of its components. We are
on the verge of a technological breakthrough with the introduction
of AI and we need to dispose off toxic e-waste from our home before
we pile up more and more e-waste. We are is dire need of
introducing a customer awareness campaign because of lack of
interest and knowledge regarding e-waste.
Proper disposal of used electronic gadgets
E-waste is a growing problem for us in India. As an 132cr
strong economy, we produce e- waste in large quantities.
It is very important to dispose off waste in a pragmatic
manner.
Ways to dispose off e-waste:
1. Give Back to Your Electronic Companies and Drop Off
Points
2. Visit Civic Institutions
3. Donating Your Outdated Technology
4. Sell Off Your Outdated Technology
5. Give Your Electronic Waste to a Certified E-Waste
Recycler
Identity theft
Identity theft occurs when someone uses our identity or
personal information—such as our name, our license, or
our Unique ID number—without our permission to
commit a crime or fraud.
Common Ways ,how our Identity Can Be Stolen:
- Data Breaches
- Internet Hacking
- Malware Activity
- Credit Card Theft
- Mail Theft
- Phishing and Spam Attacks
- WiFi Hacking
- Mobile Phone Theft
- ATM Skimmers
Common Ways our Identity is Used:
- Thieves open fraudulent credit card accounts in our name.
- Thieves use our credit cards or account numbers to make purchases.
- Thieves sell our personal information on the dark web—Unique ID no, credit card, and account information—to commit credit fraud, medical fraud and more. Thieves file fraudulent taxes and/or steal our tax refunds.
- Thieves know your account passwords, bank PIN numbers or other passwords to access your computer
How to protect identity online:
- Protect our computer and smartphone with strong, upto-date security software Learn to spot spam and scams.
- Use strong passwords.
- Monitor our credit scores
- Freeze our credit.
- Only use reputable websites when making purchases
Steps immediate after identity theft :
- Contact our lender, notify them of the fraud. If it’s a credit card account, freeze your card immediately.
- Register an FIR with the police.
- Follow up with the lender to ensure that the fraudulent transaction (if it appears) the FIR is removed.
Unique IDs and biometrics
Biometrics is the science of analyzing physical or behavioral
characteristics specific to each individual in order to be able to
authenticate their identity.
- Physiological measurements -They can be either morphological or biological. These mainly consist of fingerprints, the shape of the hand, of the finger, vein pattern, the eye (iris and retina), and the shape of the face, for morphological analyses.
- Behavioral measurements -The most common are voice recognition, signature dynamics (speed of movement of pen, accelerations, pressure exerted, inclination), keystroke dynamics, the way objects are used, gait, the sound of steps, gestures, etc. A unique identifier (UID) is a numeric or alphanumeric string that is associated with a single entity within a given system. UIDs make it possible to address that entity, so that it can be accessed and interacted with.
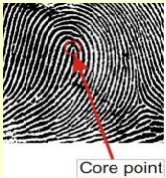
Unique ID Generation: An image processing tool like MATLAB is used for the conversion of
fingerprint to unique ID in the form of a QR code. The most important step
is to identify a unique point in the fingerprint which will serve as a
reference point. All the other minutia features will be calculated with this
point as the origin. And hence the fingerprint of the same individual taken
in different orientations will all produce the same ID. Core point of the
fingerprint is one such unique point.
After finding the core point, the minutia points are extracted by taking the
core point as reference. there will be a large number of minutiae. But only
a few minutiae which are absolutely unique for that particular fingerprint is
needed to generate the unique ID. For this only the minutiae which are
inside a Region Of Interest (ROI) centered around the core point are taken.
The reliability of biometrics
- Biometric authentication relies on statistical algorithms. It therefore cannot be 100 %-reliable when used alone. "false rejections" or "false acceptances“.
Multi-modal biometrics:
- For a number of years now, the use of several biometrics in combination, for example the face and the iris or the iris and fingerprints, has made it possible to reduce error rates considerably.
How accurate is biometrics?
- The technical challenges of automated recognition of individuals based on their biological and behavioral characteristics are inherent in to the transformation of analog (facial image, fingerprint, voice pattern...) to digital information (patterns, minutiae) that can then be processed and compared/matched with effective algorithms.
Gender and disability issues while teaching/using computers
Gender Issues
- Preconceived notions – Notions like “boys are better at technical and girls are good at humanities.
- Lack of interest
- Lack of motivation
- Lack of role models
- Lack of encouragement in class
- Not girl friendly work culture
Issues list above are not intentionally created , hence need a different type
of handling
- There should be more initiative program for girls to take computer subject.
- Film and tv censor board should ensure fair representation of female role models in tv or cinema
- In practical room they should be more helped and assisted
Disability Issues
- Unavailability of teaching materials/aids
- Lack of special needs teachers
- Lack of supporting curriculum
Possible Solution
- Enough teaching aids must be prepared for specially abled students
- Must employ special needs teachers
- Curriculum should be designed with students with specially abled students in mind.
Society Law Ethics : Part-I
Unit 4: Society, Law and Ethics (SLE-2)
INTRODUCTION:
Intellectual property rights
Intellectual Property (IP) – is a property created by a person or
group of persons using their own intellect for ultimate use in
commerce and which is already not available in the public
domain.
Examples of IP Property which are, an invention relating to a
product or any process, a new design, a literary or artistic work
and a trademark (a word, a symbol and / or a logo, etc.)
Intellectual Property Right (IPR) is the statutory right granted
by the Government, to the owner(s) of the intellectual property
or applicant(s) of an intellectual property (IP) to exclude others
from exploiting the IP commercially for a given period of time,
in lieu of the discloser of his/her IP in an IPR application.
Why should an IP be protected?
- IP is an assets and can be exploited by the owner for commercial gains any manner.
- IP owner may intend to stop others from manufacturing and selling products and services which are dully protected by him.
- IP owner can sell and/or license the IP for commercial gains .
- IP can be used to establish the goodwill and brand value in the market.
- IP can be mention in resumes of it’s creator and thus show competence of it’s creator.
- IPR certificate establishes legal and valid ownership about an intellectual property.
Kinds of IPRs
- Patent (to protect technologies - The Patent Act)
- Trade Mark (to protect words, signs, logos, labels – The Trade Mark Act)
- Design (to protect outer ornamental configuration – The Designs Act)
- Geographical Indications (GI) (to protect region specific product–The Geographical Indications of Goods Act)
- Copyright (to protect literary and artistic work –The Copyright Act)
IPRs are protected in accordance with the provisions of
legislations of a country specific. In India, IPRs can be
protected and monopolized as per the act. Some of
them are:-
1- The Patent Act, 1970,
2- The Designs Act, 2000,
3- The Trade Mark Act, 1999,
4- The Geographical Indications of Goods Act, 1999,
5- The Copyright Act, 1957,
6- Protection of Integrated Circuits Layout and Designs
Act, 2000,
7- Protection of Plant Varieties and Farmers Rights Act,
2001, and also Trade Secret.
Plagiarism
Plagiarism is
“the act of presenting the words, ideas, images,
sounds, or the creative expression of others as it is
your creation or your own.”
The word plagiarism is derived from the Latin word
plagiare, which means to kidnap or abduct.
Why is it important to understand Plagiarism?
- Plagiarism is stealing of intellectual property
- Plagiarism is cheating
- Plagiarism is an Academic offence.
- Plagiarism is Academic theft!
Types of Plagiarism :
1 Intentional Plagiarism:
- Copying other’s work.
- Borrowing/buying assignments.
- Cut , paste from electronic resources.
- Downloading essays/text from the Internet and presenting as our own work
2 Unintentional Plagiarism:
- Not knowing how to acknowledge or incorporate sources of information through proper paraphrasing, summarizing and quotation.
- Careless copying or cutting and pasting from electronic databases.
- Quoting excessively .
- Failure to use our own “voice”.
How to avoid plagiarism ?
- Use your own ideas.
- Cite the sources-When someone else's ideas are used, always acknowledge the sources and tell your reader WHERE THE IDEAS ARE FROM.
- Rewrite other's ideas in your own words.
- Take careful notes 5: Develop your writing skills.
Digital rights management
DRM – A scheme that controls access to copyrighted material using
technological means.
It means applying technology on copyrighted material in such a way that
it can be used or it remain in read only mode but further
production/copying is restricted.
HOW DIGITAL RIGHTS MANAGEMENT WORKS
Most general, digital rights management includes some codes that
prohibit copying, or codes that limit the time or number of devices a
certain product can be accessed.
Publishers/authors of content creators use an application that encrypts
e-book, content, data, software, media or any other copyrighted material.
Only those with the decryption keys can access the material.
Different ways to protect your content, software, or product
- Restrict /prevent users from editing / saving/sharing /forwarding our content.
- Restriction from printing. E.g. some document or artwork may only be printed up to a limited number of times.
- Restriction of screenshots capture
- Set an expiry date on your document or media, after which the user will no longer be able to access it or opening of any document for fixed limited times.
- Lock through ip address,means media accessible in india can’t be accessed in any other country.
- Watermark artworks and documents in order to establish ownership and identity.
CHALLENGES OF DIGITAL RIGHTS MANAGEMENT
Not everybody agrees with digital rights management. For instance,
users who pay for music on specific app would love to be able to listen
to the song on any device or use it in whatever way they wish.
BENEFITS OF DIGITAL RIGHTS MANAGEMENT
- It educates users about copyright and intellectual property.
- It helps make way for better licensing agreements and technologies.
- It helps authors retain ownership of their works.
- It helps protect income streams.
- It help secure files and keep them private
Licensing
A software license is a document that provides
legally binding guidelines to the person who holds
it for the use and distribution of software.
It typically provide end users with the right to make
one or more copies of the software without
violating copyrights. It also defines the
responsibilities of the parties entering into the
license agreement and may impose restrictions on
how the software can be used. Software licensing
terms and conditions usually include fair use of the
software, the limitations of liability, warranties and
disclaimers and protections.
Benefits of Using Licensed Software
- Using Unlicensed Software Against the Law
- The Right Software License Can Save our Money
- We can Receive Around-The-Clock License Support
1. Creative Commons (CC)License: is an internationally active non-profit organization to
provide free licenses for creators to use it when making their work available to the
public in advance under certain conditions.
Every time a work is created, such as when a journal article is written or a
photograph taken, that work is automatically protected by copyright. Copyright
protection prevents others from using the work in certain ways, such as copying
the work or putting the work online.
CC licenses allow the creator of the work to select how they want others to use the
work. When a creator releases their work under a CC license, members of the
public know what they can and can’t do with the work. This means that they only
need to seek the creator’s permission when they want to use the work in a way not
permitted by the license.
The great thing is that all CC licenses allow works to be used for educational
purposes. As a result, teachers and students can freely copy, share and
sometimes modify and remix a CC work without having seeking the permission of
the creator
The Pros of using a Creative Commons License:
- Our work will be freely available online and people can share and use as per permissions applied on creative work.
- Further improvement in creative work(open source code also) is possible ,if permission is given.
- Our original Copyright is protected and can be modified within the parameters of the Creative Commons licensing regime.
The Cons of using a Creative Commons License:
- We cannot revoke a Creative Commons License once given. Only subsequent uses will not be permitted.
- if someone profits from our work (provided we have not given a Noncommercial license/ attribute license), we can’t ask for compensation or a license fee
- The Copyright of derivative works can be ambiguous. If someone uses your work to develop a new work and their ‘updated’ work is substantially different, there is an argument that the initial Creative Commons License no longer applies. So think first before attaching a Creative Commons License to work.
2. GPL - General Public License(GNU GPL), is the most commonly used free
software license, written by Richard Stallman in 1989 of Free Software
Foundation for GNU Project. This license allows software to be freely
used(means freedom for use,not price wise free), modified, and redistributed
by anyone. WordPress is also an example of software released under the
GPL license, that’s why it can be used, modified, and extended by anyone.
Core values of GPL software are :
- Anyone can download and run the software.
- Anyone can modify it.
- Anyone can redistribute free copies of the software.
- Anyone can distribute modified versions of the software.
- One of the primary aspects of the GPL is copyleft.
- Copyleft is a play on the word copyright, but with similar concept. Means same protection is applied over the softwares developed over the GPL software. For this reason any work based on WordPress inherits the GPL license.
- The GPL itself is under the copyright ownership of the Free Software Foundation (FSF), a tax-exempt charity organization founded by Stallman's GNU project in order to generate funding for free software development.
Advantages of publishing software under GPL (General Public License):
- Regular feedback from users helps in the development of software in new areas.
- Open source software aids to the free development of several other open source software.
- It will get technical support from the developer’s community.
- The cost of software maintenance will be reduced as the volunteers’ increases.
- Bugs can be identified easily as the number of people working on it increases.
- It is first Copyleft license created for the open source community.
- Open source product itself will tempt the users to try and use it.
Disadvantage of using the GPL license
- If GPL licensed product is used in any commercial product then the entire product has to be released as open source. Most of the companies set a ban to use GPL product.
- Lots of people aren't aware of the stringent terms of GPL.
- Its extremely viral.
- If your project contains a component that contains a component then whole project is subject to the GPL too.
3. The Apache License: is a free and open source software (FOSS) licensing
agreement from the Apache Software Foundation (ASF). Beginning in 1995,
the Apache Group (later the Apache Software Foundation) Their initial
license was essentially the same as the old BSD license. Apache did
likewise and created the Apache License v1.1 - a slight variation on the
modified BSD license. In 2004 Apache decided to depart from the BSD
model a little more radically, and produced the Apache License v2.
Main Features Of The Apache License:
copy, modify and distribute the covered software in source and/or binary
forms
exercise patent rights that would normally only extend to the licensor
provided that:-
- all copies, modified or unmodified, are accompanied by a copy of the license.
- all modifications are clearly marked as being the work of the modifier.
- all notices of copyright, trademark and patent rights are reproduced accurately in distributed copies.
Open Source
In general, open source means any program whose
source code is made available publicly for use or
modification as users or other developers see fit.
Open source software is usually made freely
available.
Following criteria must be met for open source:
Source code must be included.
- Anyone must be allowed to modify the source code.
- Modified versions can be redistributed.
- The license must not require the exclusion of other.
Example of Open source software:
- As Operating system – linux,Ubuntu
- As dbms – mysql,mongodb
- As Programming language – java,php,python
- As internet browser/webserver –chromium, firefox / apache http server,apache tomcat
Open Data
Open data is data which can be accessed, used and shared by any
one to bring about social, economic and environmental benefits.
Open data becomes usable when made available in a common ,
machine-readable format.
Following criteria must be met for open data:-
- Must be licensed to permit people to use and share.
- It should not have limitation to use in any form.
- It must be free to use but cost should be reasonable.
- It can be reused and re distributed.
The 5 basic principles of open data decided in G8 summit in 2013
are:-
1. Open data by default
2. Should be in quality and in quality as well
3. Usable by all
4. Release data for improved governance
5. Release data for innovation
Privacy is the aspect of information technology which deals with the ability of an organization or individual to determine what data in a computer system can be shared with third parties.
Privacy law - Regulations that protects a person's/organization’s data private and governs collection, storage, and release of his or her financial, medical, and other personal information to third party.
Classification of privacy laws:
Why Privacy Matters
Privacy Laws
Privacy is the aspect of information technology which deals with the ability of an organization or individual to determine what data in a computer system can be shared with third parties.
Privacy law - Regulations that protects a person's/organization’s data private and governs collection, storage, and release of his or her financial, medical, and other personal information to third party.
Classification of privacy laws:
- General privacy laws that have an overall bearing on the personal information of individuals
- Specific privacy laws that are designed to regulate specific types of information. E.g Communication privacy laws, Financial privacy laws,Health privacy laws,Information privacy laws ,Online privacy laws ,Privacy in one’s home.
Why Privacy Matters
- To limit on Power- of company who hold data.
- To respect for Individuals
- To maintain Appropriate Social Boundaries
- To maintain Freedom of Thought and Speech of person whom data belong
- To maintain Freedom of Social and Political Activities of person whom data belong
Privacy threats
1. Web Tracking
2. Data collection
3. Lack of security
4. Connected everything
5. Public Wi-Fi
6. Government spying
7. Social networking
The (Indian) Information Technology Act, 2000: deals with the issues relating to
payment of compensation (Civil) and punishment (Criminal) in case of wrongful
disclosure and misuse of personal data and violation of contractual terms in
respect of personal data.
1. Under section 43A of the (Indian) Information Technology Act, 2000, a body
corporate who is possessing, dealing or handling any sensitive personal data or information. The Government has notified the Information Technology Rules,
2011. The Rules only deals with protection of "Sensitive personal data or
information of a person", which includes such personal information which
consists of information relating to:-
- Passwords
- Financial information such as bank account or credit card or debit card or other payment instrument details
- Physical, physiological and mental health condition;
- Sexual orientation
- Medical records and history
- Bio-metric information.
2. Under section 72A of the (Indian) Information Technology Act, 2000, disclosure
of information, knowingly and intentionally, without the consent of the person
concerned and in breach of the lawful contract is punishable with imprisonment
for a term extending to three years and fine extending to Rs 5,00,000.
Fraud
Computer fraud is using a computer and/or internet to
take or alter electronic data, or to gain unlawful use of
a computer/internet.
Illegal computer activities include phishing, social
engineering, viruses, and DDoS attacks.
With the growth in online services and internet use, there
are many opportunities for criminals to commit scams and
fraud. These are dishonest schemes that seek to take
advantage of unsuspecting people to gain a benefit (such
as money, or access to personal details). These are often
contained in spam and phishing messages.
Common types of online scams include:
- Unexpected prize scams,
- Unexpected money scams,
- Dating or romance scams,
- Threats and extortion scams,
- Jobs and investment scams, and
- Identity theft. Do not respond to online scams or fraud. If you receive an email or SMS which looks like a scam, the best thing to do is delete it.It is the best solution for online scam.
Cyber crime
Any crime that involves a computer and a network is
called a “Computer Crime” or “Cyber Crime.
Or in other term ,it is a crime in which a computer is the
object of the crime (hacking, phishing, spamming) or is
used as a tool to commit an offense (child pornography,
hate crimes).
STEPS TO PROTECT YOURSELF AGAINST CYBER CRIME:-
1. Make sure your security software is current – and
update it regularly.
2. Lock or log off your computer when you step away.
3. Go offline when you don’t need an internet connection.
4. Consider sharing less online.
5. Think twice about using public Wi-Fi.
6. When in doubt, don’t click.
Phishing
Phishing is a cyber attack that uses disguised email as a
weapon.The attackers masquerade as a trusted entity of
some kind, The goal is to trick the email recipient into
believing that the message is something they want or
need — recipient fills/send sensitive information like
account no, username, password etc. , then attacker use
these.
How to prevent phishing:
- Always check the spelling of the URLs before click
- Watch out for URL redirects, that sent to a different website with identical design
- If receive an email from that seems suspicious, contact that source with a new email, rather than just hitting reply
- Don't post personal data, like your birthday, vacation plans, or your address or phone number, publicly on social media.
Illegal downloading
Illegal downloading is obtaining files or computer
resources that w do not have the right to use from the
Internet. Copyright laws prohibit Internet users from
obtaining copies of media that we do not legally
purchase. These laws exist to prevent digital piracy,
much of which is generally conducted through Internet
file sharing.
How to prevent illegal downloading:
Movie piracy has actually decreased significantly
through BitTorrent and other traceable methods, as the
adoption curve of Netflix (and other) streaming options
has increased. The answer there is simple - make it
cheaper and easier to access media in a "legal" manner,
and more people will utilize those paths than the "illegal"
paths.
Child pornography
Child pornography is considered to be any depiction of a
minor or an individual who appears to be a minor who is
engaged in sexual or sexually related conduct. This
includes pictures, videos, and computer-generated
content. Even altering an image or video so that it
appears to be a minor can be considered child
pornography.
Child pornography is a crime in India. IT Act, 2000 &
Indian Penal Code, 1860 provides protection from child
pornography.The newly passed Information Technology
Bill is set to make it illegal to not only create and transmit
child pornography in any electronic form, but even to
browse it.
Cyber forensics
Cyber forensics is a way or an electronic discovery
technique which is used to determine and reveal technical
criminal evidence. Various capabilities of cyber forensics
are.
• Computer forensics
• Computer exams.
• Data analysis.
• Database study.
• Malware analysis.
• Mobile devices.
• Network analysis.
• Photography.
• Video analysis
IT Act 2000
The Information Technology Act, 2000 provides legal recognition to
the transaction done via an electronic exchange of data and other
electronic means of communication or electronic commerce
transactions.Some of sections under it act 2000 are given below.
Wednesday, September 25, 2019
Python-MySQL Connectivity
INTRODUCTION:
The Python Programming language has powerful features for database programming. It supports various databases like MySQL, Oracle, Sybase, PostgreSQL etc.
To establish connectivity between Python and MySQL, we require Python Database Interfaces and API.
Steps to install the connector are as follows:-
after this wait for a while MySQL -Connector shall download and will be installed on your System. Now to check whether it has been properly installed or not :-
after completing the installation of MySQL connector , the next step to establishing connection between MySQLdb and Python. for this :-
The Python Programming language has powerful features for database programming. It supports various databases like MySQL, Oracle, Sybase, PostgreSQL etc.
To establish connectivity between Python and MySQL, we require Python Database Interfaces and API.
Steps to install the connector are as follows:-
- Go to the folder where Python is installed in your PC.
- Open Folder Python 37-32
- Open > Scripts
- Press Shift+ Click Right Button of Mouse
- Click on option " open Command Window here"
- type> python -m pip install mysql-connector
- Go to command prompt and write path as C:\Users\YourName\Appdata\Local\Python\Python37-21\Scripts\ python -m pip install mysql-connector
Here Yourname means Username of your PC
after this wait for a while MySQL -Connector shall download and will be installed on your System. Now to check whether it has been properly installed or not :-
- Open Python Shell and Type
- >>> import mysql.connector
- >>>
if no error message gets displayed , means driver has been installed successfully.
Before creating database connectivity kindly ensure MYSQL should be installed in your system.
MySQL Module for PYthon Version can be downloaded from:
http://sourceforge.net/projects/mysql-python
ESTABLISHING CONNECTION
after completing the installation of MySQL connector , the next step to establishing connection between MySQLdb and Python. for this :-
- Create a new script fie in Python, type the following code and run it.
import mysql.connector
mydb=mysql.connector.connect(host="localhost",user="root",passwd= "root")
print (mydb)
if the output as shown below is obtained , means the connection has been established successfully.
RESTART: C:\Users\Admin\AppData\Local\Programs\Python\Python36-32\dbconct.py
<mysql.connector.connection.MySQLConnection object at 0x022607B0>
>>>
Note : the default MySQL user name is : root and Password "" (Blank) if you have not defined at the time of MySQL installation in your PC.
How to create table at run time
mycursor=mydb.cursor()
mycursor.execute("create table student(rollno int(3) primary key, name varchar(20),age int(2))")
On successful execution of above program a table named student with three fields rollno,name,age will be created in school database.
We can check student table in mysql shell also,if required.
How to change table structure/(add,edit,remove colum of a table) at run time
To modify the structure of the table we just have to use alter table query.Below program will add a column mark in the student table.
import mysql.connector
mydb=mysql.connector.connect(host="localhost",user="root",passwd="root" ,
database="school")
mycursor=mydb.cursor()
mycursor.execute("alter table student add (marks int(3))") mycursor.execute("desc student")
for x in mycursor:
print(x)
Above program will add a column marks in the table student and will display the structure of the table.
How to search records of a table at run time
Below statement demonstrate the use of select query for searching specific record from a table.
import mysql.connector
mydb=mysql.connector.connect(host="localhost",user="root",passwd="root",
database="school")
mycursor=mydb.cursor()
nm=input("enter name")
mycursor.execute("select * from student where name='"+nm+"'")
for x in mycursor:
print (x)
Above statements will prompt a name from user,as user type the name ,that name is searched into the table student with the help of select query .result will be shown with the help of mycursor collection.
How to fetch all records of a table at run time
import mysql.connector
mydb=mysql.connector.connect(host="localhost",user="root",passwd="root"
,database="school")
mycursor=mydb.cursor()
mycursor.execute("select * from student")
myrecords=mycursor.fetchall()
for x in myrecords:
print (x)
MySQLCursor.fetchall() Method
The method fetches all (or all remaining) rows of a query result set and returns a list of tuples. If no more rows are available, it returns an empty list.
How to fetch one record of a table at run time
import mysql.connector
mydb=mysql.connector.connect(host="localhost",user="root",passwd="root"
,database="school")
mycursor=mydb.cursor()
mycursor.execute("select * from student")
row=mycursor.fetchone()
while row is not None:
print(row)
row = mycursor.fetchone()
MySQLCursor.fetchone() Method
UNDERSTANDING ABOVE CODE:
import mysql.connector // importing mysql connector files
mysql.connector.connect () // method of MySQL connector Python with required parameters.
host="localhost" // This is the server name or IP address non which MySQL is running .if you are running on localhost, then its Ip address is 127.0.0.0
User=" root" // This is the username that you use to work with MySQL Server. The default username for the MySQL database is "root".
Password="root" // Password is given by the user at the time of installing the MySQL database. if no password is assigned then leave it blank " '.
Database="School" // it is the name of database to which connectivity is to be established.
Cursor object :
The MySQLCursor class instantiates objects that can
execute
operations such as SQL statements.
Cursor objects interact with
the MySQL
server using a MySQLConnection object.
How to create
cursor object and use it
import mysql.connector mydb=mysql.connector.connect(host="localhost",user="root",passwd= "root")
mycursor=mydb.cursor()
mycursor.execute ("create database if not exists school")
mycursor.execute("show databases")
for x in mycursor:
print(x)
Through line
4 we
are
creating a database named school
if it is
already not created with the help of cursor
object.
Line 5
executes the
sql query
show databases and
store
result
in
mycursor
as
collection ,whose values
are
being fetched
in x
variable
one by
one.
On execution
of above
program school database is created and a list
of available databases
is shown.
How to create table at run time
Table creation is very easy ,if we are already well versed in sql table creation then we have to just pass the create table query in execute() method of cursor object. But before table creation we must open the database.Here we are opening database school(through connect() method) before student table creation.
import mysql.connector mydb=mysql.connector.connect(host="localhost",user="root",passwd= "root" , database="school")mycursor=mydb.cursor()
mycursor.execute("create table student(rollno int(3) primary key, name varchar(20),age int(2))")
On successful execution of above program a table named student with three fields rollno,name,age will be created in school database.
We can check student table in mysql shell also,if required.
How to change table structure/(add,edit,remove colum of a table) at run time
To modify the structure of the table we just have to use alter table query.Below program will add a column mark in the student table.
import mysql.connector
mydb=mysql.connector.connect(host="localhost",user="root",passwd="root" ,
database="school")
mycursor=mydb.cursor()
mycursor.execute("alter table student add (marks int(3))") mycursor.execute("desc student")
for x in mycursor:
print(x)
Above program will add a column marks in the table student and will display the structure of the table.
How to search records of a table at run time
Below statement demonstrate the use of select query for searching specific record from a table.
import mysql.connector
mydb=mysql.connector.connect(host="localhost",user="root",passwd="root",
database="school")
mycursor=mydb.cursor()
nm=input("enter name")
mycursor.execute("select * from student where name='"+nm+"'")
for x in mycursor:
print (x)
Above statements will prompt a name from user,as user type the name ,that name is searched into the table student with the help of select query .result will be shown with the help of mycursor collection.
How to fetch all records of a table at run time
import mysql.connector
mydb=mysql.connector.connect(host="localhost",user="root",passwd="root"
,database="school")
mycursor=mydb.cursor()
mycursor.execute("select * from student")
myrecords=mycursor.fetchall()
for x in myrecords:
print (x)
MySQLCursor.fetchall() Method
The method fetches all (or all remaining) rows of a query result set and returns a list of tuples. If no more rows are available, it returns an empty list.
How to fetch one record of a table at run time
import mysql.connector
mydb=mysql.connector.connect(host="localhost",user="root",passwd="root"
,database="school")
mycursor=mydb.cursor()
mycursor.execute("select * from student")
row=mycursor.fetchone()
while row is not None:
print(row)
row = mycursor.fetchone()
MySQLCursor.fetchone() Method
This method retrieves the next row of a query result set and returns a single sequence, or None if no more rows are available. By default, the returned tuple consists of data returned by the MySQL server, converted to Python objects.
MySQLCursor.fetchmany() Method rows = cursor.fetchmany(size=1)
This method fetches the next set of rows of a query result and returns a list of tuples. If no more rows are available, it returns an empty list.
How to delete record of a table at run time
import mysql.connector
mydb=mysql.connector.connect(host="localhost",user="root",passwd="root"
,database="school")
mycursor=mydb.cursor()
mycursor.execute("delete from student where rollno=1")
mydb.commit()
In above program delete query will delete a record with rollno=1.commit()
method is necessary to call for database transaction.
How to update record of a table at run time
import mysql.connector
mydb=mysql.connector.connect(host="localhost",user="root",passwd="root"
,database="school")
mycursor=mydb.cursor()
mycursor.execute("update student set marks=99 where rollno=2")
mydb.commit()
In above program update query update the marks with 99 of rollno=2 Students are advised to develop menu driven program using above concepts for better understating of python mysql database interface.
Manage Database Transaction
Database transaction represents a single unit of work. Any operation which modifies the state of the MySQL database is a transaction.
Python MySQL Connector provides the following method to manage database transactions.
commit –MySQLConnection.commit() method sends a COMMIT statement to the MySQL server, committing the current transaction.
rollback – MySQLConnection.rollback revert the changes made by the current transaction.
AutoCommit – MySQLConnection.autocommit value can be assigned as True or False to enable or disable the auto-commit feature of MySQL. By default its value is False.
Manage Database Transaction
try:
conn = mysql.connector.connect(host='localhost', database='school',
user='root', password='root')
conn.autocommit = false cursor = conn.cursor()
sql_update_query = """Update student set marks = 95 where rollno = 2""" cursor.execute(sql_update_query)
print ("Record Updated successfully ") #Commit your changes
conn.commit()
except mysql.connector.Error as error :
print("Failed to update record to database rollback: {}".format(error)) #reverting changes because of exception
conn.rollback() finally: #closing database connection.
if(conn.is_connected()):
cursor.close() conn.close()
print("connection is closed")
In above program if update query is successfully executed then commit() method will be executed otherwise exception error part will be executed where revert of update query will be done due to error.At finally we are closing cursor as well as connection.To rollback or commit we have to set autocommit=false,just like conn.autocommit = false in above program otherwise rollback will not work.
SQL Commands
Grouping Records in a Query
Some time it is required to apply a Select query in a group of records instead of whole table.
We can group records by using GROUP BY <column> clause with Select command. A group column is chosen which have non-distinct (repeating) values like City, Job etc.
Generally, the following Aggregate Functions [MIN(), MAX(), SUM(), AVG(), COUNT()] etc. are applied on groups.
|
Name
|
Purpose
|
|
SUM()
|
Returns the
sum of given column.
|
|
MIN()
|
Returns the
minimum value
in the given column.
|
|
MAX()
|
Returns the
maximum value
in the given column.
|
|
AVG()
|
Returns the
Average value
of the given column.
|
|
COUNT()
|
Returns the
total number of values/ records as per given
column.
|
Aggregate Functions & NULL
Consider a table Emp having following records as-
Null values are excluded while (avg)aggregate function is used
|
Emp
|
||
|
Code
|
Name
|
Sal
|
|
E1
|
Mohak
|
NULL
|
|
E2
|
Anuj
|
4500
|
|
E3
|
Vijay
|
NULL
|
|
E4
|
Vishal
|
3500
|
|
E5
|
Anil
|
4000
|
SQL Queries Result of query
mysql> Select Sum(Sal) from EMP; 12000
mysql> Select Min(Sal) from EMP; 3500
mysql> Select Max(Sal) from EMP; 4500
mysql> Select Count(Sal) from EMP; 3
mysql> Select Avg(Sal) from EMP; 4000
mysql> Select Count(*) from EMP; 5
An Aggregate function may applied on a column with DISTINCT or ALL keyword. If nothing is given ALL is assumed.
Using SUM (<Column>)
This function returns the sum of values in given column or expression:
mysql> Select Sum(Sal) from EMP; 12000
mysql> Select Min(Sal) from EMP; 3500
mysql> Select Max(Sal) from EMP; 4500
mysql> Select Count(Sal) from EMP; 3
mysql> Select Avg(Sal) from EMP; 4000
mysql> Select Count(*) from EMP; 5
Aggregate Functions & Group
An Aggregate function may applied on a column with DISTINCT or ALL keyword. If nothing is given ALL is assumed.
Using SUM (<Column>)
This function returns the sum of values in given column or expression:
|
mysql>
|
Select
|
Sum(Sal) from EMP;
|
|
mysql>
|
Select
|
Sum(DISTINCT
Sal) from EMP;
|
|
mysql>
|
Select
|
Sum ( Sal) from EMP where City=‘Jaipur’;
|
|
mysql>
|
Select
|
Sum ( Sal) from EMP Group By City;
|
|
mysql>
|
Select
|
Job, Sum(Sal) from EMP Group By Job;
|
Using MIN (<column>)
|
This functions returns the Minimum value in the
given column.
|
Subscribe to:
Comments (Atom)